Configure 2FA For MediaWiki: Difference between revisions
| Line 49: | Line 49: | ||
[[File:G Verified Page.png|800px|thumb|none|Yay, it works]] | [[File:G Verified Page.png|800px|thumb|none|Yay, it works]] | ||
Log off now, and log back in, and you should be prompted for username & password, and then prompted for a six digit code. This code is time sensitive, | Log off now, and log back in, and you should be prompted for username & password, and then prompted for a six digit code. This code is time sensitive, so it will be different each time you log in, and will expire after a short time. | ||
Congratulations, you are now one of the cool kids. | Congratulations, you are now one of the cool kids. | ||
Revision as of 20:53, 5 December 2024
How to use OATHAuth in Mediawiki
Configure OATHAuth
The version of Mediawiki I'm using has OATHAuth preinstalled. To configure your Mediawiki instance to allow users to enable two-factor authentication simply add
wfLoadExtension( 'OATHAuth' );
to the end of the LocalSettings.php file located in the root of the MediwWiki directory. Then restart your HTTP server. In my case I simply run
sudo systemctl restart httpd
Install oathtool
There are a number of OATH clients on the market, but I decided to just install the oathtool command line tool on my Fedora based laptop, by running
sudo dnf install oathtool.x86_64
Apple has the same functionality built into the Passwords app, but as I only login from my Fedora based laptop, it's easier to run a command and copy the output to my clipboard. You do you.
I'm using the Vector 2020 skin, so if your screen looks different, you're likely using a different skin.
Enable 2FA
I created an account called Test2fa to illustrate how to enable Two-Factor Aythentication. After you login with your own username & password, open your Preferences dialog.
In the User Profile tab of the Preferences dialog, hit the Manage button in the Two-Factor Authentication section.
Next, enable the Time-based One Time Password by hitting the Enable button.
It makes you login again because reasons.
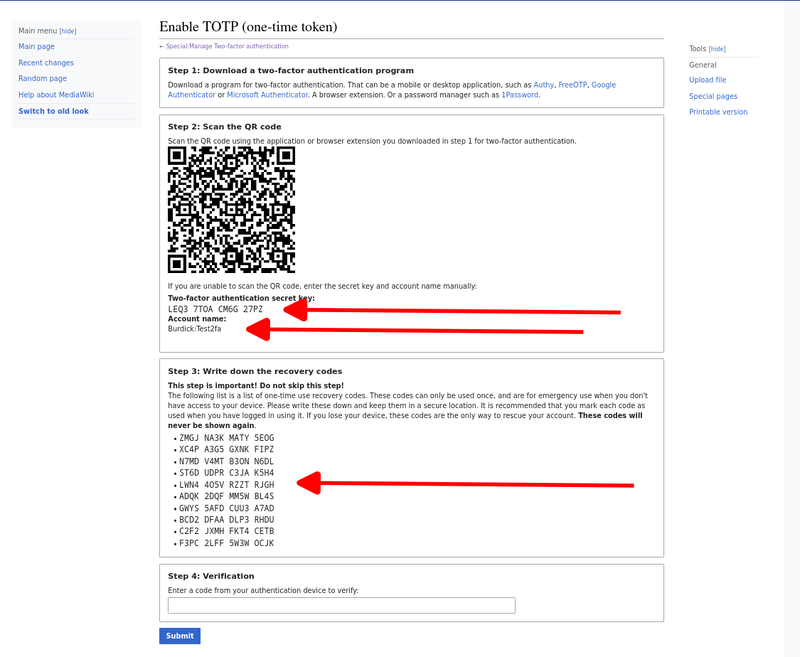
You will be presented with a page of information. This information will never change. The secret key will be used by the oauthtool to generate the 6 digit TOTP. Save it all, including the recovery codes, in case you screw things up.
This is just a temporary account I've since deleted. Keep all your information secret.
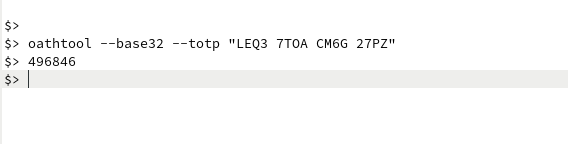
Open a terminal window, and run the oauth tool as follows.
oathtool --base32 --totp "LEQ3 7TOA CM6G 27PZ"
This will generate the six digit code that you will use during your new login process. I created a one-line script with this command so I don't need to remember the arguments. Obviously you will want to give this script 700 permissions so nobody can see it but you.
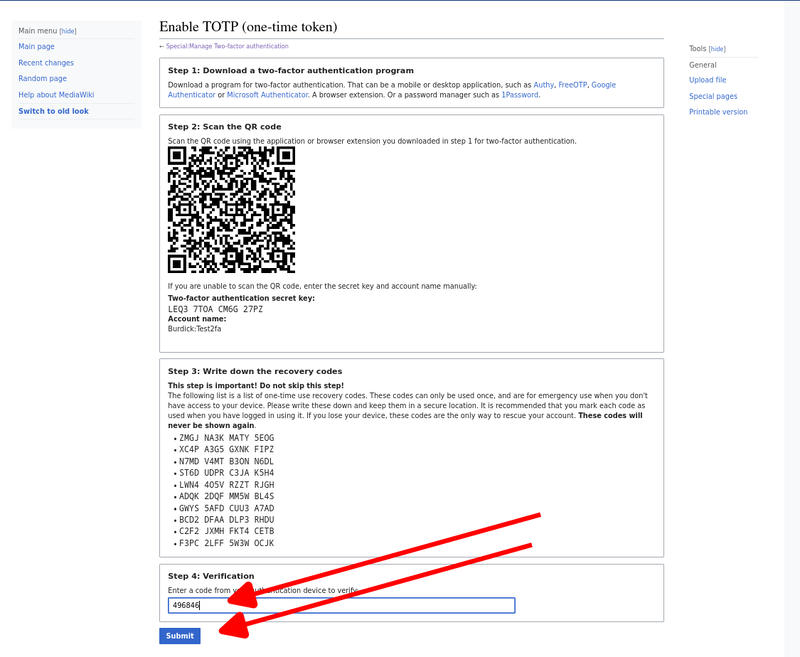
Use that generated six digit code to verify that TOTP is working.
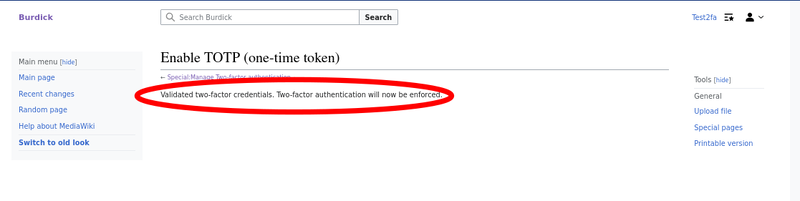
You should see a page saying that it worked, and that two-factor authentication will be enforced.
Log off now, and log back in, and you should be prompted for username & password, and then prompted for a six digit code. This code is time sensitive, so it will be different each time you log in, and will expire after a short time.
Congratulations, you are now one of the cool kids.